What is Hybrid Azure AD Join?
Hybrid Azure AD Join allows you to manage your on-premises computers using both your on-premises Active Directory and Azure Active Directory. This provides several benefits, including:
- Conditional Access: You can use Conditional Access to enforce access policies based on user identity, device risk, and other factors.
- Intune: You can enroll your devices in Microsoft Intune for mobile device management (MDM) and mobile application management (MAM).
- Autopilot: You can use Autopilot to provision and configure new devices automatically.
Implementing Hybrid Azure AD Join is straightforward and can be configured using Azure AD Connect. The steps for a managed domain are different from those for a federated domain.
- Managed domain: A managed domain is a domain that you manage in Azure AD.
- Federated domain: A federated domain is a domain that you manage on-premises and federate to Azure AD.
The Azure AD Connect wizard creates a Service Connection Point (SCP) in Active Directory in the path Configuration – Services – Device Registration. The keywords attribute of the SCP holds two values: AzureADid and AzureADName. These values contain your tenant ID and tenant name, respectively.
This post will focus on the managed domain scenario.
Target deployment
Above instructions both tell you how to implement Hybrid Azure AD Join for all your devices at once. Preferably, we would like to test the roll-out on a subset of our devices.
1. From Azure AD: Add the user to the azure group so they have permission to enroll devices into intune. The user must log into the device in order to enroll. More on mdm user scope: https://allthingscloud.blog/configuring-intune-mdm-user-scope-and-mam-user-scope/ The group created for the lab is [Windows_MDM_User_Scope_COBO] 2. On premise AD: Add device to [IntuneJoin] group so the device will inherit the GPO to auto enroll into Intune MDM. (This policy enable automatic MDM enrollment using default Azure credentials) 3. Run script to insert the following registry hive via sccm or any other endpoint management platform. The script will place reg key on the device in order Hybrid Join it to your tenant. (My tenant name is blue929.com for this lab) PowerShell: reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\CDJ\AAD" /v TenantId /t REG_SZ /d xxxInsert_Tenant_ID_Herexxx /f reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\CDJ\AAD" /v TenantName /t REG_SZ /d Blue929.com /f These keys have the same effect as configuring it through Azure AD Connect. They have the same prequisites as the other implementation methods. Two of them are often forgotten: • The OU where the devices resides need to be sync’ed in Azure AD Connect • Firewall & Proxy should be configured to allow the discovery traffic
Inside Hybrid Azure AD Join
What exactly happens when you configure a device to start his Hybrid Azure AD Join? Windows actually activates the task ‘Automatic-Device-Join’ that is located in ‘Microsoft – Windows – Workplace Join’.

This task attempts to join to Azure Active Directory and tries to find out what the TenantID & TenantName is he needs to use. He will search in two places:
- Registry with Path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\CDJ\AAD]
- SCP in Active Directory
If we look into the triggers of this task, there are two different triggers:
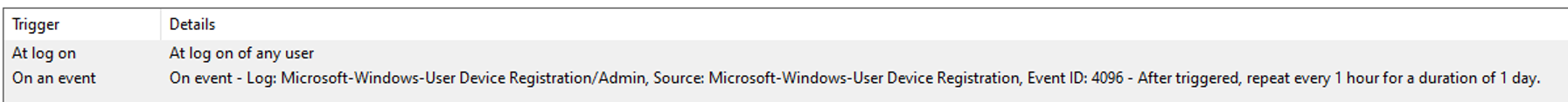
- If a user logs into the device
- Or if event ‘4096’ is logged. What is event 4096? If we go looking, we can find it in event viewer with as path ‘Microsoft – Windows – User Device Registration – Admin’.
So if you want to troubleshoot an Hybrid Azure AD Join, you can manually trigger this task to speed up the process. What does the scheduled task do? It executes the dsregcmd command!
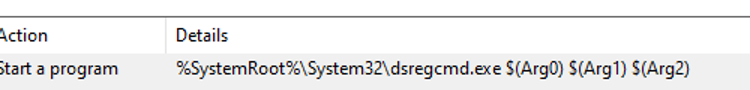
Dsregcmd
During Hybrid Azure AD Join projects, the dsregcmd command is your best friend. This command can help you find out if a device is already registered, unjoin a device or manually start the join process.
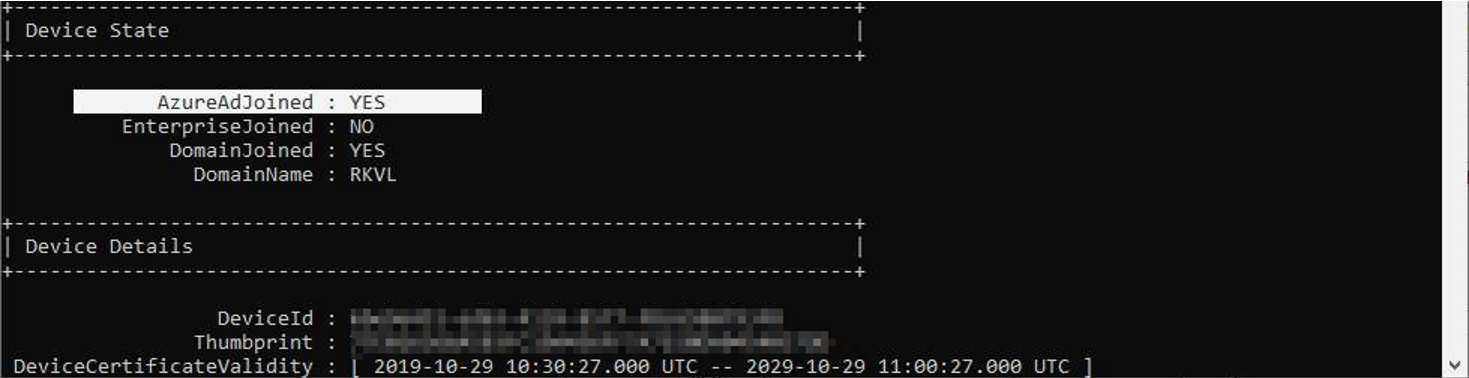
/status /status is the easiest to use parameter of the command and will show you if a device is already Hybrid Azure AD Joined. The PC in the output below isn’t Hybrid Azure AD Joined yet, because you can see the ‘AzureADJoined’ status is ‘No’.

The output of an Hybrid Azure AD Joined looks like this. As you can see, here the value of ‘AzureADJoined’ is Yes. Further down you can also find information about the Azure Primary Refresh Token, which is used for Single Sign-on.
/leave If you are experiencing unexpected issues with the Hybrid Join or you want roll back. You can execute the dsregcmd /leave commando. This will not unjoin the computer from the on-premises domain, it will only unjoin the computer from Azure AD.
/join If you want to manually join the computer to Azure AD, you can execute the dsregcmd /join command. This command should be run in SYSTEM context (using psexec for example) and will force an attempt to Azure AD. If you couple this parameter with the ‘/debug’ parameter. You are able to see error codes why this process is failing.
Event viewer
When troubleshooting an Hybrid Azure AD Join, the Event Viewer provides you with loads of information. All Join information is stored in ‘Microsoft – Windows – User Device Registration – Admin’
What are some common Event ID and how can these help you troubleshoot your implementation?
• 306 – Automatic Registration succeeded
○ Your device has been Joined :). You are all set! Validate using the dsregcmd /status command or in the Azure AD portal.
• 212 – Error happened while accessing registry
○ This error will occur when you haven’t configured the registry values that I mentioned in Controlled roll-out. If you are using the SCP in Active Directory to publish your tenant info, you will also receive this error. But in that case, there is nothing to worry about.
• 100 – Discovery Request Sent
○ In this step the computer sends a request to Azure AD. If you are seeing errors in the event viewer that happen seconds later this event, it means the computer is having trouble sending this discovery request. This points to network issues most of the times.
• 101 – Discovery Operation was Successful
○ This means your computer has contacted Azure AD successfully. If you see this, your network engineer has done his job!
• 102 – Initialization of join request was successful
○ In here you will find your DomainName. If this information isn’t correct or it is empty, there is something wrong with your SCP or registry keys.
• 105 – Complete Join Response was successful
○ The join has been finalized
• 106 – Post Join Tasks for the AAD Authentication Package completed successfully
○ Your device is being doing some more work after the join (sending device info etc).
• 111 – Registration status has been successfully flushed to disk
○ Registration was successfully saved to your computer.
The following errors are all related to network issues. If you are having issues, verify that you have configured the proxy to allow these requests and that the firewall isn’t blocking the Microsoft URLs. All the URLS can be found here.
• 223 – WINHTTP_STATUS_CALLBACK_REQUEST_ERROR – Error Code 0x80072ee2
• 201 – Discovery Operation Failed with exit code 0x80072ee2
• 309 – Failed to discover Azure DRS Service. Exit code 0x801c0021
• 304 – Automatic registration failed at join phase. 0x801c0021
Then there is another error I have seen a lot ‘0x801c03f2’. This error can be seen in two different situations.
- The device is excluded in the sync of Azure AD Connect due to filtering
- The user hasn’t logged back in since the previous join step.
These two problems are fairly easy to fix. For the first one: configure you Azure AD Connect correctly so the OU of the device is included and the object not filtered out because of a customer rule.
I have seen the same issue while the device was in the right OU and I was 100% sure it was being sync’ed. For this, I have found that starting the ‘Automatic-Device-Join’ task resolves this issue. In my understanding, this error is shown because the computer has done all the discovery steps and told AzureAD it’s ready to join, but AzureAD hasn’t sync’ed the device yet. So if you are seeing this issue on a subset of your devices. Just take a coffee, take a long sip, wait until the next day and follow-up once more!
The $ in the device name
If you are renaming your device on-prem, it’s possible the device shows up with a ‘$’ after its name. Check out this blog post for more information.
It is also worth trying a [dsregcmd /leave] or [dsregcmd /debug /leave], give it some time then join it again.
From my experience in production, there were devices with the trailing $ to the device name, the devices were already renamed before any attempts to hybrid join. Upon checking on Entra, the device was stuck on a pending state with the following errors 204 and 304. The solution was to restart the device and automatic registration went through. If all else fails, delete the device from Entra then reimage it.
Error number 204:

Error number 304
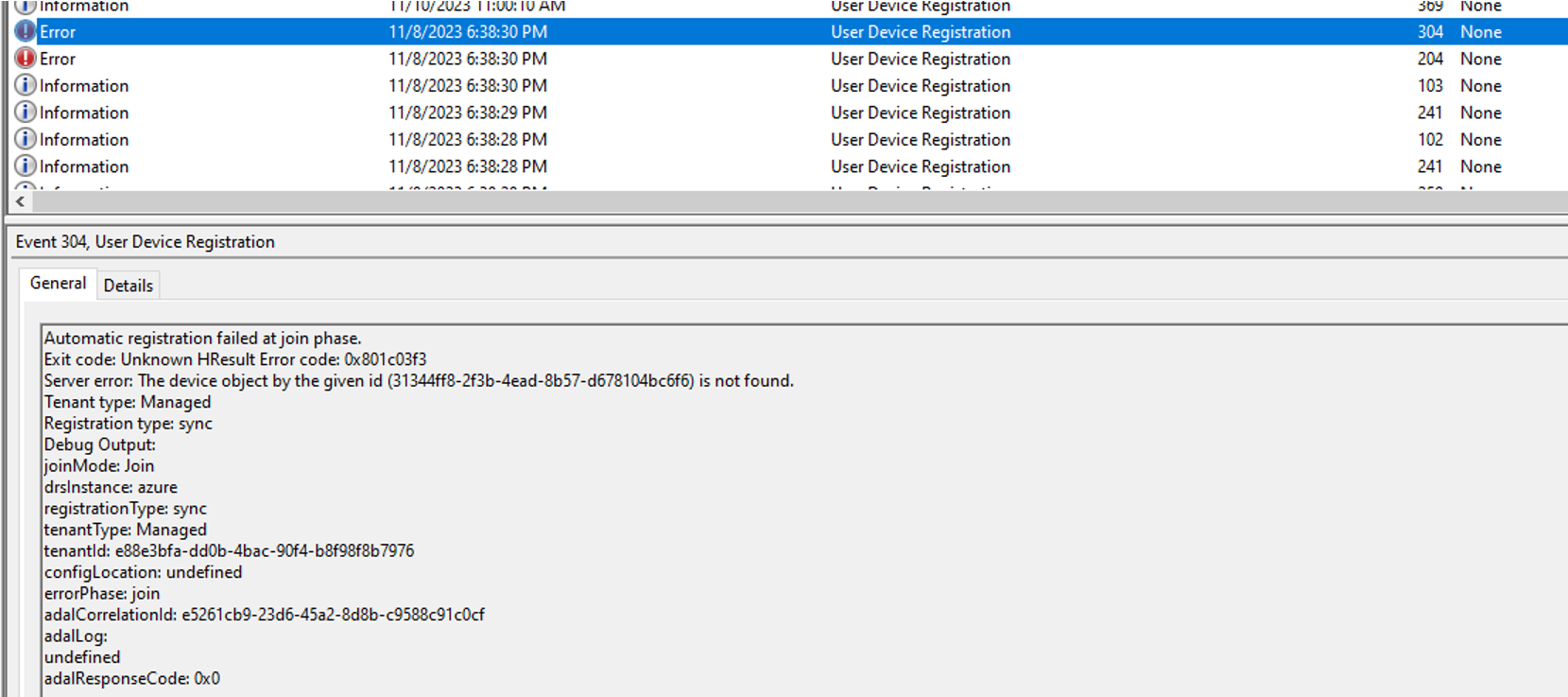
Once device restarts, it was able to register and hybrid join successfully.


Error 76
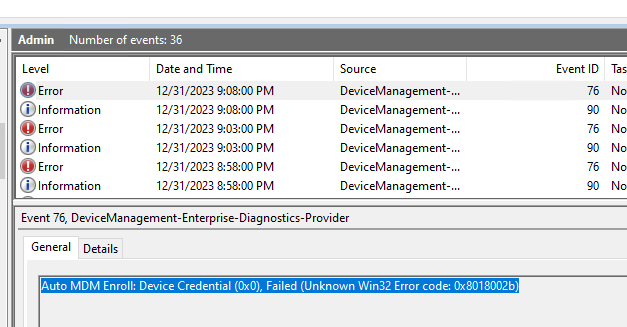

- Make sure to have Azure AD Premium and Microsoft Intune License assigned to user
- Make sure user are in the appropriate group and have permission to enroll devices into Intune
- Sign out or restart device to test out user credentials
- Possibly device limit for user, either rise the device limit for the user or remove a device. Alternative is to assign a DEM (Device enrollment manager) role to a spare account and log in using that account.
- If rollout is targeted for specific group, are the following registry hive present:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\CDJ\AAD” /v TenantName /t REG_SZ /d Blue929.com /f
- Make sure GPO policy is NOT set to device credentials

- Please ensure that your users are logging in with their Azure AD credentials and not their on-premise credentials, such as contoso/UPN. If users are attempting to log in with their on-premise credentials, you need to adjust the on-premise UPN to match the Azure AD UPN. This will allow them to log in with the correct credentials and successfully enroll their devices. If your Azure AD domain is mycontoso.com, you need to add this as an Alternative UPN Suffix under Domains and Trusts in Active Directory. Once this is done, when users log in, enrollment should happen immediately. If not, the device will not be able to identify the user’s Azure AD credential.
- Be sure to also add xxxx.onmicrosoft.com through AD Domain and trust even if primary domain is blue929.com. There may be resources referencing the default generated onmicrosoft.com domain.


- Trigger Gpupdate then dsregcmd /join to test hybrid join on device and then dsregcmd /status to check status. The following below are DSREGCMD switches
- /? : Displays the help message for DSREGCMD
- /status : Displays the device join status
- /status_old : Displays the device join status in old format
- /join : Schedules and monitors the Autojoin task to Hybrid Join the device
- /leave : Performs Hybrid Unjoin
- /debug : Displays debug messages
- Check scheduled task of hybrid join:
- The main scheduled task for initiating and completing the Hybrid Join process is “Automatic-Device-Join” under \Microsoft\Windows\Workplace Join.
Unknown Win32 Error code: 0x80192efd- System Proxy!
This is due to the system proxy not being correctly configured. Many times proxy configurations and/or PAC files are set mostly in the user context and sometimes the system context gets neglected. To fix, simply run this command from an elevated command window (updating of course with your environment specific details):
netsh winhttp set proxy proxy.mycompany.com:8080 To check what your current system level proxy settings are set to, run this: netsh winhttp show proxy After running the first command, give the system a reboot and the automatic enrollment process should kick off again and successfully complete this time. You should then see more success messages in Event Viewer including this one: You can reset the proxy back to defaults by running: netsh winhttp reset proxy If you are still getting error after this then you may have more issues on the proxy side blocking or not properly redirecting the correct Microsoft URLs for AAD and Intune.
The device is not appearing in Entra or in Intune
According to Intune time, this may take a while for the device to be fully enrolled and managed in Intune. Depending on the amount of objects, give it at least 10 to 30 minutes. The device object not found is normal since the object is not yet synced over to Entra.


Trouble signing in
Make sure the registered state is not set to PENDING -(Give it some time) and then run dsregcmd /status again. When the registered state of a device is pending, the device can’t complete any authorization or authentication requests, such as requesting a Primary Refresh token for single sign-on
Dual state
If your Windows 10 or newer domain joined devices are Azure AD registered to your tenant, it could lead to a dual state of hybrid Azure AD joined and Azure AD registered device. We recommend upgrading to Windows 10 1803 (with KB4489894 applied) or newer to automatically address this scenario.
DSREGTOOL- Deep dive
Run device registration tool script to troubleshoot device join (ex: pending state) if the normal dsregcmd cmdlets does not resolve the issue. The DSREGTOOL is a powerful tool that checks all the perquisites needed and even makes recommendations on troubleshooting device registration with Azure.
Download the tool here – open powershell and run the script: https://github.com/Azure-Samples/DSRegTool/archive/refs/heads/main.zip
Information and instructions here: https://learn.microsoft.com/en-us/samples/azure-samples/dsregtool/dsregtool/

Had trouble trying to hybrid join a device, only to realize the following url cannot be reached.

Source:
https://365bythijs.be/2019/11/02/troubleshooting-hybrid-azure-ad-join/
https://learn.microsoft.com/en-us/samples/azure-samples/dsregtool/dsregtool/
https://learn.microsoft.com/en-us/samples/azure-samples/dsregtool/dsregtool/
