Android personal device enrollment, grants you access to a limited yet appropriate set of device management configurations and actions. This allows you to safeguard work-related data without interfering with the personal data or applications of the device user. There are few enrollment types available from Intune:
Android Enterprise: Android Enterprise presents a range of enrollment choices that furnish users with the latest and most secure functionalities. It supports GSM devices that allows BYOD, COBO, COPE, COSU enrollment. By enrolling in Android Enterprise with a personally-owned or corporate-owned work profile, users gain access to a suite of features and services that distinctly segregate personal applications and data from work-related ones. This enrollment method also imparts enhanced management capabilities (Conditional access, app protection policy, etc..) and privacy safeguards for individuals utilizing their personal Android devices for work purposes.

Android Open Source Project (AOSP): The AOSP approach targets devices that does not utilize Google Mobile Services (GMS). GMS devices are preinstalled with google api and apps like Chrome, Youtube, Gmail, etc.. . The purpose of AOSP is to enroll devices that can serve as kiosk-style, single-purpose tablets, or display signage, unaffiliated with any particular user or be assigned to a single user. Their sole purpose is for organizational tasks and not intended for personal use. Android device administrator: Legacy android enrollment model for older devices. Google no longer supports this method. Superseded by Android Enterprise enrollment.
Pro:
- Provides a secure partition on personal device that only allows access to company deployed apps and resources. This segmentation results in no integration with any native apps for the personal device, keeping work and personal data completely separate.
- Features include reset passcode and remote lock for device once enrolled.
- Any application or data synced on work profile gets removed once device is retired.
Con:
- No integration with native apps
- Outlook calendar DOES NOT sync with native calendar app. It must be manually added. (This is by design with Intune and native android app not compatible]
Goal: Enroll a personal android device into Intune. Then assign the appropriate policies and apps. This guide assumes that the general Intune prerequisite settings are already configured (General Intune UEM Prerequisite)
Prerequisites
- The device must have Android 8.0 and later, including devices secured by Samsung KNOX Standard 2.4 and later with GSM (Google Mobile Services)
- Create Security Groups (assigned and dynamic)
- Configure General notification (optional)
- Link managed google play store account
- Configure Enrollment Type Profile
- Compliance Policy (Custom Policy, Default policy and Notifications) (optional)
- Device Configuration profile (Optional)
- Application deployment (Optional)
- App protection Policies (Optional)
- App Configuration Policies (Optional)
- Conditional access policy (Optional)
Create Security Groups (assigned and dynamic)
Once the license are in place, create security groups in Entra (Azure AD), assign E3/E5 license to those groups. Dynamic Groups do not need license in this lab. I recommend assigning license based on USER and not devices. **User should NOT be a member of both BYOD and COBO group.
Below are the following groups created for this lab.
Assigned group (Assigned groups requires IT Admin to manually add users):
Android_BYOD_Assigned – (Users here can enroll personal Android devices)
Dynamic Device Groups (Automatically provides a list of devices):
To create a dynamic group > select new group > membership type (Dynamic User or Dynamic Device) > Add Dynamic Query. (I suggest validating rule for the query to test that it works correctly)
(dynamic groups automatically filters device based on a query provided. This group is not required for enrollment but good to have when Admin need to review all personal or corporate devices *optional).
Android_Device_BYOD_Dynamic – Query personal android devices

Configure General notification
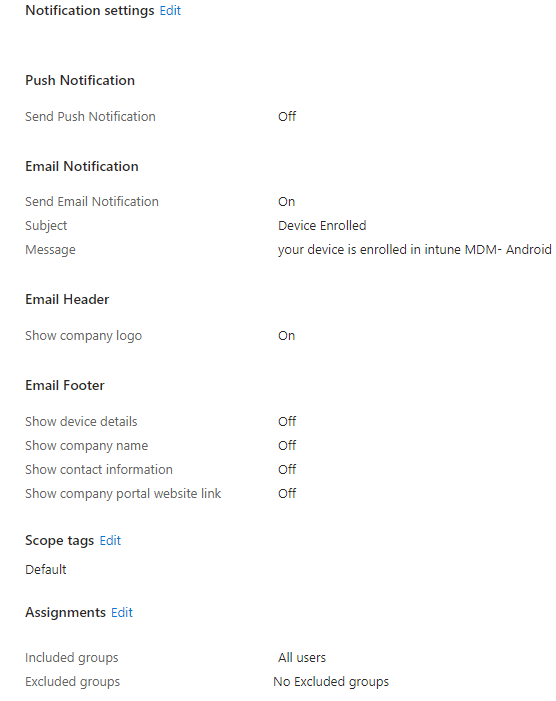
Configure email and push notifications to be sent to users after they enroll. Notifications improve security by notifying users if someone enrolls a device with their credentials. IT admins can also use enrollment notifications to send users a welcome email or on boarding information following enrollment.
Navigate to Intune admin center > Devices > Android > Android Enrollment > Enrollment notifications
Under Android Enterprise Notification > create new notification
Configure depending on organization needs. For example, I have it configure to send email notification on devices enrolled and the target is all users.
Link a Managed google play to Intune first
In order to deploy apps and manage enterprise devices, a spare Gmail account must be used to sign into the play store and have it link to Intune. Do not use a personal account, instead, create a company Gmail account that can be used. The account cannot be associated with G-suite domain.
Navigate to Intune admin center > devices > android > android enrollment > managed Google Play

Choose “Launch Google to Connect now.”
Input your company’s name and the name of your Enterprise Mobility Management (EMM) provider, ensuring that Microsoft Intune is correctly displayed. Proceed and click confirm.
*Microsoft company portal, Microsoft Authenticator, Intune, managed home screen will be available in admin center once the process is done.

Set up enrollment profile
By default, the enrollment of personally-owned work profile devices is activated, eliminating the need for additional steps.

Compliance Policy (Custom Policy, Default policy and Notifications)
Review Default compliance policy:
For any device enrolling under a MDM, it must meet a security baseline requirement and has to be secured in order to access company data. Note that there is Default Device compliance policy in place that Intune applies to all devices regardless of whether a compliance policy is created or not. This default policy is a base minimum so we must create an additional custom policy to enforce to all devices.
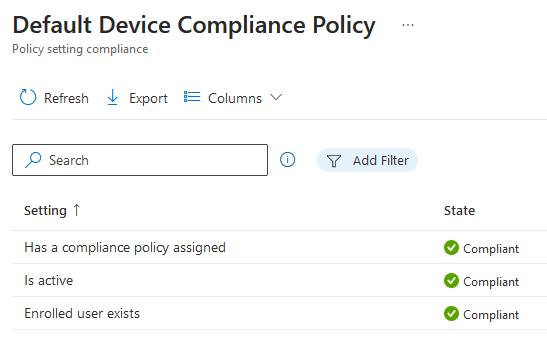
Has compliance Policy assigned- The setting is tied to "Mark device with no compliance policy assigned as" - Not compliant so it checks if there is a custom compliance policy assigned to device. If it finds one, state is green. Is active - relies on the default 30 days grace validity period. The device must check into Intune within 30 days, check in refresh every 8 hours. Check in depends if devices has internet connection and not whether the primary user is logged in or not. For shared devices with multiple users, the device just have to connect to internet. Enrolled User exists- Checks if the primary user exist with a valid license for the enrolled device. For shared devices or devices enrolled under a DEM (Device Enrollment Manager), I suggest changing the primary user. I do not recommend deleting any users from Entra ID (Azure AD).
Creating a custom policy:
Navigate to Intune admin center > Endpoint Security > Device Compliance > compliance policy setting > toggle “Not Compliant”
This will mark all devices with no manually assigned compliance policy as not compliant. So we must create an compliance policy for every type of OS, which is highly recommended.
Compliance status validity period– The device must check into Intune within 30 days, check in refresh every 8 hours. After 30 days past and there is no active sync, device is marked non-compliant. This is tied to “Is Active” setting under default device compliancy policy.

Navigate back to Policies > Create policy > edit the properties to meet company requirement.
My compliance policy for personal device is to block rooted device, require a minimum OS version, and in order to access company resources, a minimum 4 digit password to get into the device.
The assigned user group will be Android_BYOD_Assigned.

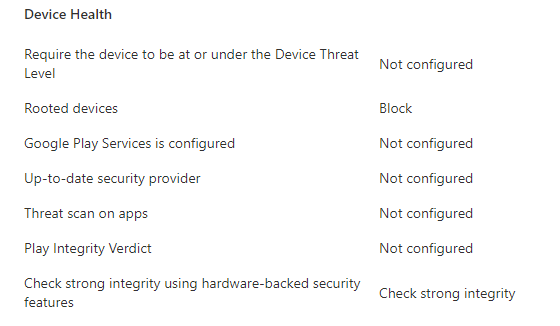

If device is not compliant, user will get an email and push notification and the device will be marked non-compliant. (IT Admin can put a grace period of days that settings can be fixed to become compliant. The default value is 0, which immediately marks the device as non-compliant if restrictions are not met)

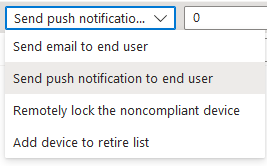
Actions for noncompliance - Each device compliance policy includes one or more actions for noncompliance. These actions are rules that get applied to devices that don’t meet the conditions you set in the policy. Examples of actions include: • Sending email alerts to users and groups with details about the noncompliant device. You might configure the policy to send an email immediately upon being marked as noncompliant, and then again, periodically, until the device becomes compliant. • Remotely lock devices that have been noncompliant for some time. • Retire devices after they’ve been noncompliant for some time. This action marks a qualifying device as ready to be retired. An admin can then view a list of devices marked for retirement and must take an explicit action to retire one or more devices. Retiring a device removes the device from Intune management and removes all company data from the device.
Compliance policy Notifications: (*Optional- Email user if device is non-compliant)
Create a notification message template
To send email to your users, create a notification message template. When a device is non compliant, the details you enter in the template is shown in the email sent to your users.
- In the Intune admin center, select Devices > Compliance policies > Notifications > Create notification.
- Enter the following information for the Basics step:
- Name: Contoso Admin
- Email header – Include company logo: Set to Enabled to show your organization’s logo.
- Email footer – Include company name: Set to Enabled to show your organization’s name.
- Email footer – Include contact information: Set to Enabled to show your organization’s contact information.
- Company Portal Website Link: Set to Disabled.
Device configuration Profiles
For even further restriction, rules can apply to users device under configuration policy > device restrictions. BYOD carries the following restrictions:
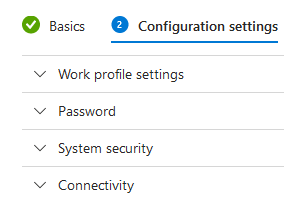
Not only is there device restrictions, there are also different profile types shown below which are configured per device.

Deploy Apps
Before enrollment starts, we will assigned required/non required apps to the device so users can immediately get to work once they are enrolled.
**The application will install itself on work profile, a separate partition from personal apps on the device. This does not conflict with the personal app. If device gets retired from Intune, the work profile apps will get removed.
Navigate to > Apps > Android > select “Add” > select managed google play app
Select Microsoft Outlook and Microsoft 365 (Office). Then proceed to configure the appropriate assignments.
The required app will get installed once the device is enrolled and updates are only downloaded once its on wifi and not in use.

Update priority: Default: Updates app if device is charging, connected to wifi, in idle state with no other updates running in the background High Priority: Push updates as soon as new release regardless of idle, wifi or charging status Postponed: postpone updates for up to 90 days.
Deploy App protection Policies (highly recommend)
App protection policies (APP) are rules that ensure an organization’s data remains safe or contained in a managed app. Works regardless if device is enrolled or not. Since identity broker is company portal, user must sign into company portal app to inherit app protection policy.
To apply restrictions and DLP rules to outlook app that gets deployed:
Navigate to Apps > App Protection policies > create policies > select Android. Target Policy to selected apps > Microsoft Outlook.
Modify it depending on preference. The settings below are just some and not all of the DLP settings that can be applied. Assign the policy to user group – Android_BYOD_Assigned
**Pin for access setting requires a Pin specifically used only to access the outlook app. This pin is different from the Phone pin.




App Configuration Policies
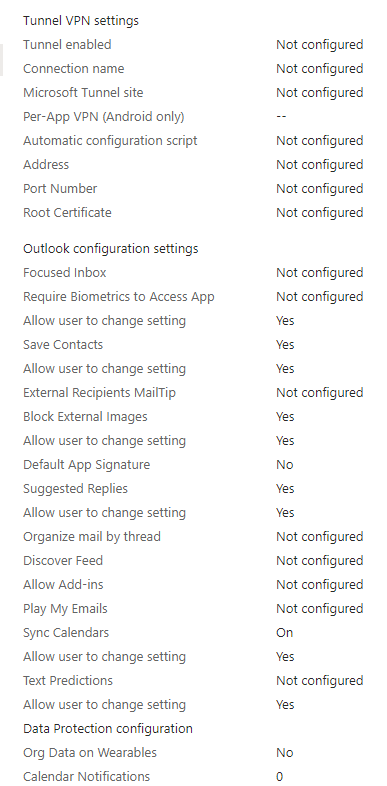
Additional DLP settings can be found under app configuration policies targeting Outlook such as VPN, S/MIME and outlook app features.
App configuration policies can also help you eliminate app setup problems by letting you assign configuration settings to a policy that is assigned to end-users before they run the app
Under app configuration policy enrollment type:
Managed app(Targets users): Delivered via through the Mobile Application Management (MAM) channel. [requires Android 9.0 or higher ]
Managed device (User or device): Delivered via mobile device management (MDM) OS channel [Intune requires Android 8.0 or higher]
Navigate to Apps > App configuration policies > add > managed apps > target Outlook app > assign to BYOD or COBO group
Conditional access policy (Highly recommend)
Given that compliance policy is a passive approach to devices that are not compliant with company policy, we will need to deploy conditional access policy to enforce compliance. Unlike a custom compliance policy that takes actions [Lock, retire or email user] for the device, conditional access provides more granular control such as blocking access to all Microsoft 365 apps, SharePoint or all cloud apps if device is not compliant.
Navigate to Intune admin center > endpoint security > conditional access > polices
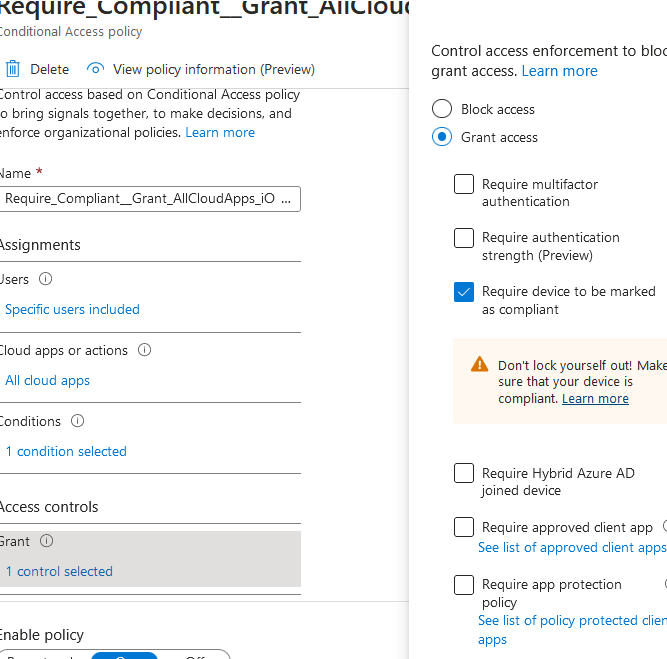
In this policy, we will block access to office 365 apps if device is not compliant for android devices. Any attempt to access any of those apps will prompt users to correct their security settings. Recommend testing this only on test group first and filter by platforms. Troubleshoot conditional access policy logs by going to endpoint security > conditional access > Sign-in Logs.
List of office 365 apps blocked are listed here.
Assignments: Users: Include: Android_BYOD_Assigned Target resources: Include: Office 365 Exclude: Microsoft Intune Conditions: Device Platforms: Android Access control: Grant: Requires device to be marked as compliant
Enrollment
Go to the Google Play store, and install the Company Portal app.
Users open the Company Portal app, and sign in with their organization credentials.
Proceed with the privacy terms, let the compliance check go through at the end and that is all for enrollment.
Note: Android users with BYOD will be utilizing OUTLOOK apps for Email, contacts and calendar UNDER WORK PROFILE (container) only. All work apps will have a brief case next to it.
Verify on Intune:
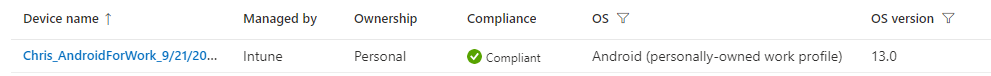
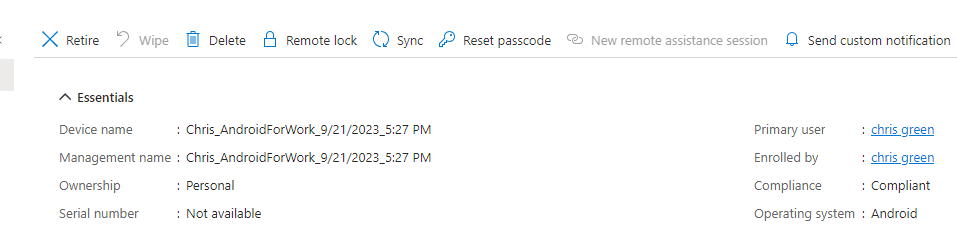
Notes: • Block Android device administrator enrollment in Enrollment restrictions if you only want users to enroll with Android Enterprise personally-owned devices with work profiles. • User should NOT be a member of both BYOD and COBO group • Identity broker is company portal • What happens if password change? User will get a notification on phone to sign in again to their apps
Source:
https://learn.microsoft.com/en-us/mem/intune/apps/app-configuration-policies-use-android
https://learn.microsoft.com/en-us/mem/intune/apps/app-protection-policy
https://learn.microsoft.com/en-us/mem/intune/user-help/enroll-device-android-work-profile
S02E07 – Manage Android Devices with Intune – A Comprehensive Guide – Leon Ashton-Leatherland (I.T)