This guide will show you how to make it more difficult for users to register their devices to Intune or Entra. It is recommended that you enable multi-factor authentication (MFA) when adding devices to Entra. When MFA is enabled, users must authenticate with a second method before they can add a device to Entra. This helps to prevent attackers from adding unauthorized devices to the domain using compromised user accounts.
Goal: Deploy conditional access policy requiring users to go through passwordless MFA when an attempt to register or join the device is triggered.
Prerequisites:
Navigate to Entra ID portal > devices > Device setting > Toggle “No” for the setting “Require MFA to register or join devices with Microsoft Entra”.

This setting will need to be disabled since it does not introduce any granular control. This setting enforces MFA when register or join devices for whole tenant. CA will be used instead.
What is the meaning of Join and register?
Join:
Joining a device to Entra means that the device must authenticated using organization account under:
- “Access school or work” setting
- bulk enrollment
- autopilot
Joining the device will put it in a “Microsoft Entra Joined” state, providing full access to company resources. The “join” state also applies to hybrid devices as well. If intune is setup, the device is managed under Intune with corporate ownership.

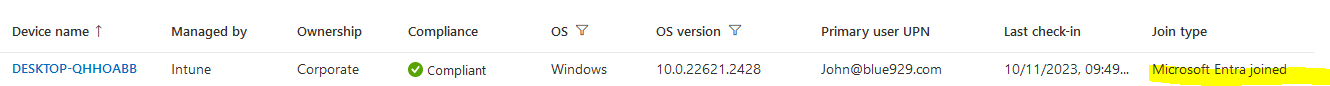
Register:
Registering a device put the device under personal ownership and is intended for BYOD scenarios. User can register their personal devices to access company resources.
Personal mobile devices must install company portal app to register their devices. Windows devices can add the organization account under settings “Access work or school account” > enter email address. (Skip the alternate actions as this will join the device and have it fully managed by Intune)

Require MFA when registering or Joining a device
Navigate to Intune portal > devices > conditional access > new policy. The policy will trigger regardless of the location and set for all platforms.
Name: [All Devices] [All Users] Require_MFA_Join_Or_Register_Devices Assignments: Users: Include: All users Target resources: Include: User actions > register or join devices Access control: Grant: Require Authentication strength (passwordless MFA + TAP)
User experience
User will need to meet MFA requirement if they want to connect their windows devices to Entra. In this lab, it will require passwordless mfa. The following picture shows the steps to “Join” the device and put it under corporate ownership. Select “Join this device to Microsoft Entra ID” to have it fully managed. Fully managed devices will inherit all of company policy.
If you only want to “register” the device and have personal ownership, simply skip the alternate actions and sign in using your organization email address.




Logs:

